About Us
Don’t trust the sender name: SMS hijacking attacks are getting smarter
DECODED: TECH, TRUTH, AND THREATS
By Art Samaniego
I’ve already posted this before, but I believe it’s timely to repost it as a growing number of people are once again falling victim to this kind of scam.
Every day, reports are surfacing about fake messages posing as banks, government agencies, and even e-wallets like GCash and Maya. These scams are becoming more convincing and more frequent, especially now that cybercriminals are exploiting loopholes in SMS technology and mobile networks.
Just recently, spoofed texts under the names “Globe” and “Maya” made rounds, tricking unsuspecting users. Many still don’t realize that just because a message looks official doesn’t mean it is.
Please read and share this article. It could save someone from financial loss or identity theft.
How cybercriminals impersonate sender IDs on text messages
Have you ever received a text message that appeared to come from a trusted source, such as your bank, a government agency, or even your e-wallet provider, only to realize later it was a scam? This deceptive practice, known as SMS spoofing or SMS hijacking, is a growing tactic used by scammers and cybercriminals to impersonate legitimate entities.
Recently, some users reported receiving fake text messages with “Globe” as the sender ID. Globe promptly warned the public that this was a case of spoofing. Spoofing involves fraudsters sending unauthorized text messages using fake cell towers to deceive recipients.
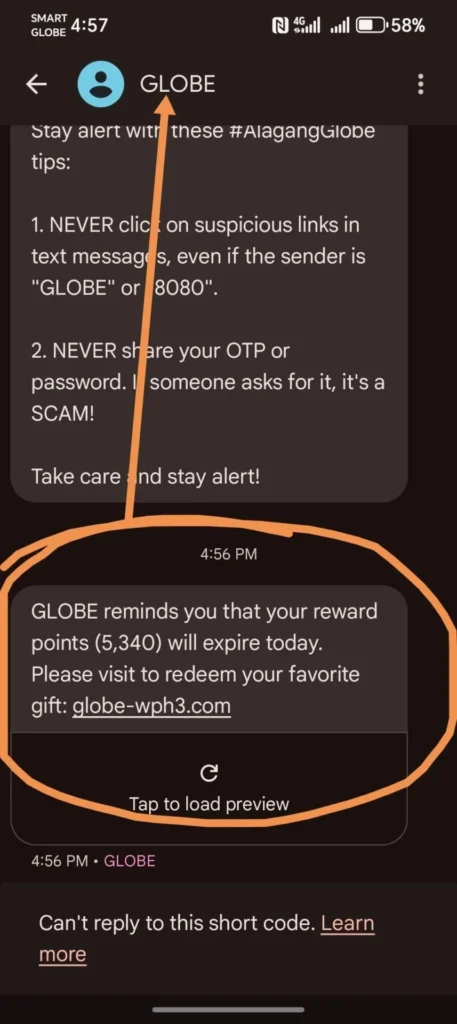
Globe explained that spoofing operates through an International Mobile Subscriber Identity (IMSI) catcher, a portable device that captures mobile users’ signals within a limited radius. This device forces their connection to downgrade to 2G, an older cellular network technology for voice calls and text messages. Since spoofed messages do not pass through Globe’s cellular network, they bypass the company’s rigorous anti-fraud filters.
Here’s how cybercriminals do it, and how you can protect yourself.
Understanding SMS hijacking
SMS hijacking is a technique where cybercriminals manipulate a text message’s “Sender ID” to make it appear as if the message comes from a trusted source. For example, a scammer might send a message that seems to be from your bank, using a sender ID that matches the bank’s name or phone number.
How It Works:
1. Exploiting SMS Protocols: SMS messages are sent using a protocol that allows the sender to specify the “Sender ID.” While this feature was designed to let businesses and organizations customize their messages, it can be exploited by malicious actors.
2. Using Third-Party Services: Scammers often use SMS gateways or platforms that allow them to set a custom Sender ID. These services can be legitimate but are misused by cybercriminals for fraudulent purposes. There are companies with insecure gateways that scammers can use to trick users into believing that it is a legitimate message from the company.
3. Global Communication Loopholes: Since SMS messages often pass through multiple networks (especially for international communication), enforcement of Sender ID authenticity can be inconsistent, making it easier for scammers to spoof identities.
4. Using IMSI Catchers: Cybercriminals may also use IMSI catchers (International Mobile Subscriber Identity catchers), which are devices designed to intercept mobile phone communications. These devices mimic legitimate cell towers, tricking nearby phones into connecting to them. Once connected, the attacker can intercept SMS messages, including one-time passwords (OTPs), enabling unauthorized access to sensitive accounts. IMSI catchers exploit vulnerabilities in older network technologies, such as 2G and 3G.
However, they are ineffective against networks that operate solely on 5G, as 5G networks incorporate enhanced encryption and authentication protocols to thwart such attacks.
BSP’s Warning on SMS Hijacking
The Bangko Sentral ng Pilpinas (BSP) has issued a public advisory to caution individuals about SMS hijacking, particularly as it poses a significant risk to financial security. Scammers can use hijacked SMS channels to get OTPs and other sensitive information, enabling unauthorized access to bank accounts or online wallets.
The BSP emphasizes the need for vigilance and proactive measures among users and financial institutions to mitigate the risks associated with this threat.
GCash, the number one e-wallet platform in the country, has also been regularly sending warnings to its subscribers not to click links sent via SMS, even if the messages appear to be from GCash, as scammers could mimic legitimate Sender IDs to deceive users. These advisories emphasize the importance of caution and verifying information before taking action.
Common tactics used by scammers
Scammers employ SMS hijacking for various schemes, such as:
Phishing: Sending fake links to websites designed to steal personal information, such as login credentials or credit card details.
Malware Distribution: Encouraging recipients to download malicious apps or files.
Payment Fraud: Pretending to be a service provider to trick users into making unauthorized payments.
How to avoid becoming a victim
1. Verify the Sender:
– Don’t rely solely on the Sender ID to verify the legitimacy of a message.
– Cross-check the information by contacting the organization directly using official contact details from their website or other trusted sources.
2. Beware of Links:
– Avoid clicking on links in unsolicited or unexpected messages.
– Instead, manually type the organization’s official website address into your browser.
3. Look for Red Flags:
– Poor grammar or spelling mistakes.
– Urgent or threatening language designed to create panic or pressure you into taking immediate action.
4. Use Security Tools:
– Enable spam and fraud detection features in your messaging app or mobile carrier settings.
– Install reputable antivirus software that can detect malicious links or attachments.
5. Report to relevant authorities if you think you’re scammed:
– The Philippine government has mechanisms to report spam or fraudulent messages, immediately call 1326 or go to the PNP Anti Cybercrime Group to report any incident of scamming .
– Inform the impersonated organization to help them take action against the fraudsters.
6. Enable Two-Factor Authentication (2FA):
– Use 2FA for sensitive accounts to add an extra layer of protection against unauthorized access, even if your credentials are compromised.
What to do if you click on a scam link
If you accidentally clicked on a fraudulent link and gave your details, it is important to act quickly to minimize the potential damage. Begin by disconnecting from the internet to prevent further data exposure; turn off both Wi-Fi and mobile data. Then, using a different device, update the passwords for any accounts that may have been compromised to ensure they remain secure.
Use antivirus software to scan your device for any malware or other threats that might have been introduced. Afterward, contact relevant authorities such as your bank, service providers, or the Cybercrime Investigation and Coordinating Center at 1326 to inform them of the incident, especially if sensitive information has been exposed. Finally, keep a close watch on your financial and online accounts for any unauthorized activities, as early detection can mitigate potential losses.
While SMS hijacking poses a significant risk, awareness and vigilance can help you stay safe. By understanding how scammers operate and following best practices to verify and secure your communications, you can reduce the likelihood of falling victim to such schemes. The BSP’s advisory serves as a critical reminder to always verify and protect your personal information. Remember, when in doubt, it’s always better to err on the side of caution and verify before you act.
